In the earlier I have written about the keys generation and the MIC verification for WPA2 Authentication. Have a look at below link for WPA2 in depth 4-way handshake analysis.
WPA2-Key-Generation and MIC Verification
We need to understand the key hierarchy and different keys that will get generated in 4-way handshake . see the below figure to know about key Hierarchy.
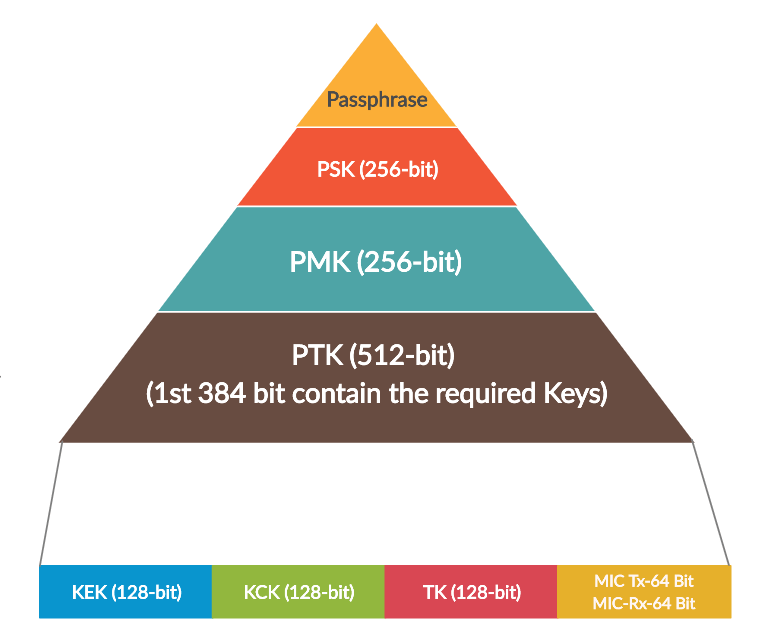
In this post we will look in to the MIC Verification/Generation procedure for WPA2-PMF/WPA3/OWE. And we will also look in to how the MIC Generation for WPA2-PMF/WPA3/OWE is different from WPA2.
PMK gets generated using SHA-1 in WPA2.
PMK gets generated using SHA-1 in WPA2-PMF.
PMK gets generated using ECDH in WPA3/OWE.
PTK gets generated using SHA-1 in WPA2.
PTK gets generated using SHA-256 in WPA2-PMF/WPA3/OWE.
MIC gets generated using SHA-1 in WPA2.
MIC gets generated using AES-CMAC in WPA2-PMF/WPA3/WPA2-PMF.
If we know the KCK [Derived from PTK], then the MIC generation Procedure for WPA2-PMF/WPA3/OWE will be the same.
Observe the below figure to check the differences between the security mechanisms. Check what algorithms are used to generate PMK, PTK, and MIC in different wireless security mechanisms.

MIC Generation for WPA2-PMF, WPA3, OWE
MIC Generation will be same for WPA2-PMF, WPA3 and OWE because they all use same MIC generation AES-CMAC. If we know the KCK for the 4-way handshake exchange then the procedure will be the same for all of them.
How easy is it Know the PTK ?
It will be easy to get the PTK when we are using WPA2 and WPA2-PMF. It will be difficult to get the PTK when we are using WPA3 and OWE. If we get the PTK then we can verify the MIC for the 4-way Handshake for WPA3.

Note that , Getting the PMK is not an easy task in WPA3 even if we have the SSID, Password, and captured 4-way Handshake. Because we will not have the private keys that were used to generate the PMK.
Also note that, Insider Attacks are still possible with WPA2, and even with WPA2-PMF (802.11w) who knows the SSID , Password and captured 4-way handshake EAPOL Frames, because all the clients will have same PMK in WPA2 and WPA2-PMF.
But with WPA3 PMF , Insider Attacks are not possible because, we can’t get the PMK without the private keys. And the each client will have separate PMK.
Now we will verify the MIC that is generated in the 4-way Handshake for WPA3/WPA2-PMF/OWE.
I took the example for WPA3 handshake and it will be same for WPA2-PMF/OWE if we know the PTK.
WPA3 Keys Generation
Here in this example, I have a PMK that got generated from the WPA3 Handshake procedure. Now we will generate the PTK using SHA-256-PRF and then we will verify the MIC.
I have a PTK that got generated for the WPA3 Handshake. Below are the contents of the PTK and length of the different Keys in the PTK.

Here is the PTK of the 4-way handshake that we are going to discuss now. Observe the below figure that has generated the required keys in our example.

PTK for the WPA3 Handshake
e4cecf6a384a15975a919295b18716ba8754791e2129dc11bca0b9f03d4d2e2ca1ae967dacdd65a145d5d95f3c6322fc702e6a4bff7f000000dc6a3541ad8883
So, the keys are
Keys
So, KCK is 1st 128 bits of the PTK i.e
KCK: e4cecf6a384a15975a919295b18716ba
KEK, is 2nd 128 bits of the PTK i.e
KEK: 8754791e2129dc11bca0b9f03d4d2e2c
TK, 3rd 128 Bits of PTK
TK : a1ae967dacdd65a145d5d95f3c6322fc
MIC Tx is next 64 bits of PTK
MIC Tx : 702e6a4bff7f0000
MIC Rx is last 64 bits of PTK
MIC Rx : 00dc6a3541ad8883
MIC Verification in WPA3 4-Way Handshake
1) M1 Message: Here AP will send the Nonce to the client and we call it as Anonce. WPA3 MIC key will be generated using AES CMAC , so the key generation algorithm used for WPA3/WPA2-PMF/OWE will be the same, and WPA2-PSK MIC generation will be different.
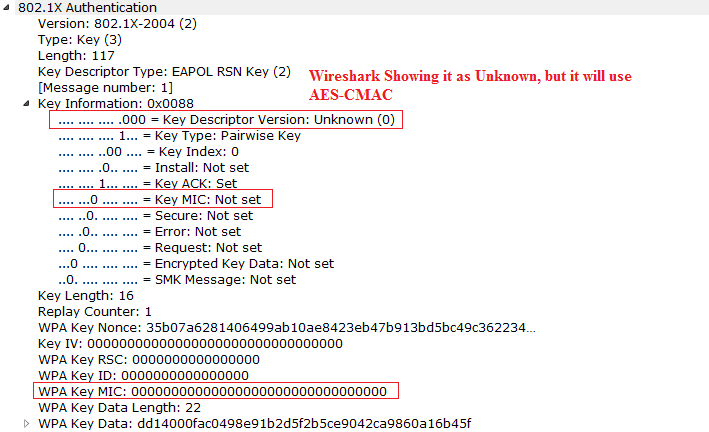
2) M2 Message: M2 Message goes from the client to AP, And Client will send the Snonce to the AP, we call it as Snonce. After this message AP also will generate the PTK. In this message AP verifies the MIC that is generated by the client. Now we will verify the MIC in M2 Message using AES-CMAC.

Now get all the M2 Data and replace the MIC value to all Zeros. And then use the KCK to generate the MIC. We have multiple ways to generate and verify the MIC.
- We can use C library to generate the MIC by properly sending the proper input to the AES-CMAC function. It is little difficult to do it , but can be done with little effort.
- We can use python program to generate the MIC. Using python program will be easier to verify the MIC.
MIC Verifcation of WPA3 using Python Program
Observe the below Python AES-CMAC program to generate the MIC.
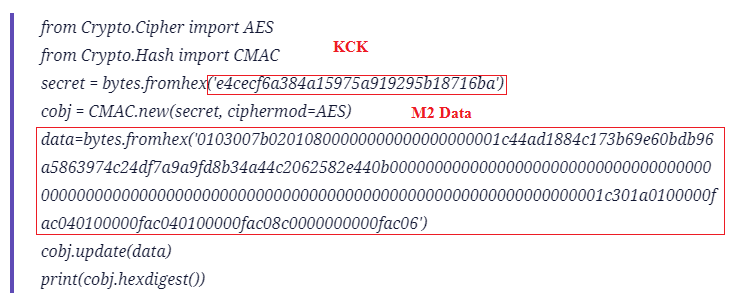
Now execute the Python program and check the MIC that is generated.

3) M3 Message: Now lets generate the MIC for the M3 Message in the 4-way Handshake. In this Message Install bit will be set to 1 in key information, so that Client will install the PTK. And generated keys will be used to encrypt the unicast/broadcast traffic.
Observe the below M3 Message and we will calculate the MIC for the M3 Packet. Here get the M3 data and replace the MIC value to all Zeros and use the KCK to generate the MIC.


If we execute the above program generated output matches with the Wireshark MIC.

4) M4 Message: We will verify the final M4 Message MIC, This M4 Goes from the Client to AP.
See the below capture to check the M4 MIC.

Below is the python program to generate MIC for M4. And is similar to the procedure that we have seen above.

Now execute the python program with the data that we collect in the M4, and we will compare the result with the sniffer capture result. It matches with the wireshark MIC.

This is all about MIC generation and Verification in a WPA2-PMF/WPA3/OWE handshake.