In the earlier posts I have written in detailed analysis about the Protected Management Frames, and also discussed why is it important to protect the management frames.
Please refer the below link to know more about the PMF.
In this post we will discuss how the Unicast Deauthentication/Disassociation request frame will get verified on the client/AP when used PMF.
Problem Description
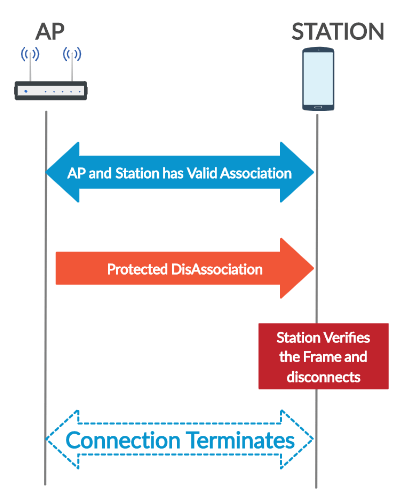
1. Here the STA and AP has the valid connection.
2. An attacker sends the Deauthentication/Disassociation notificaiton to the client with the spoofed MAC Addresses.
3. Here the STA assumes that the Deauthentication/DisAssociation came from the valid AP and terminates the session.

In the above problem, if we know the MAC Address of the station then it will be easy to disconnect the station.
So, the standard introduced new feature Protected Management Frames (802.11w), so that the client/AP verifies the deauthentication frame and checks if the frame has come from the genuine client/AP. If the verification is failed then the AP/Client simply ignores the deauthentication frames.
This management protection is enabled by default in WPA3.
We will take the example for a protected unicast Disassociation frame and then we will check how it gets verified. The verification process will be same for Protected unicast Deauthentication Frame as well.
Verification of Protected Disassociation Frame
Observe the below diagram for the successful disassociation. We will check the wireshark traffic and then we will learn how the station/AP verifies the protected disassociation frame.
Observe the below Deauthentication Frame captured from wireshark and then we will verify the data.
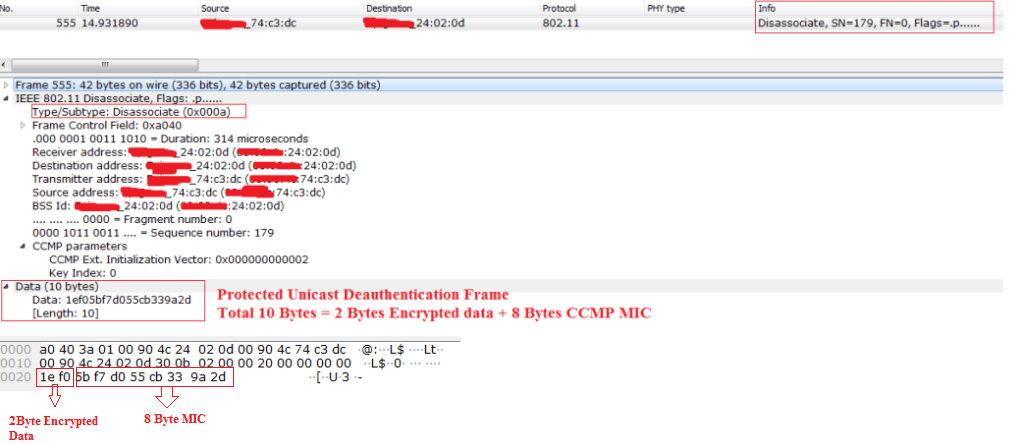
In the Deauthentication/Disassociation Frame , There will be 2 Bytes of Encrypted Data. This 2 Bytes is the Reason Code. And 8 Bytes of MIC will be sent in the Deauthenticaion or Disassociation Frame.
we have to properly get the hex data from the wireshark capture. We should have the below input to encrypt the data. Encryption or Decryption Fails if the data is wrong. And it is not an easy task to get the accurate data.
- Temporal Key that got generated at the time of 4-way Handshake. Because this is the Unicast key that encrypts the Unicast Disassociation Frame.
- Refer my old posts to know how encryption keys gets generated in WPA2 and WPA3.
- 802.11 Header Data For MIC Generation.
- We have to properly take the data , if we take wrong hex values then the decryption fails.
- Packet Number ( we have to read Packet Number from CCMP Header from wireshark capture)
- Plain text Data for CCMP (2 Bytes)
- Here 2 Bytes is going to be the hex data ( 08 00 ). This two bytes is the data that will get encrypted.
- 08 00 is the reason code
- This reason code changes based on the reason.
- Here 2 Bytes is going to be the hex data ( 08 00 ). This two bytes is the data that will get encrypted.
Plain text data is 08 00, because this is the reason code for disassociation. It has been given by the standard. We don’t see this information in the wireshark , because it gets encrypted.

The Below diagram shows the Input that we give to the CCMP Program and then the encrypted data and MIC.
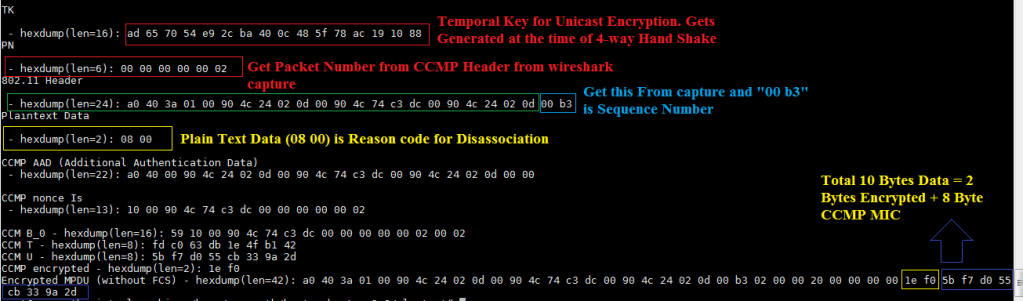
Observe the Figure 3 and Figure 5 , the Encrypted Data matches with the sniffer capture.
In the same way the receiving Station Decrypts the data.
So, This way the protected Disassociation Frames gets verified , so that the attacker can’t disassociate the connected stations from the network, because he doesn’t know the TK. The Station/AP ignores the Fake Disassociation/Deauthentication.
Decryption process is going to be the same for WPA2-PMF/WPA3/OWE or any other EAP Authentication if we know the TK.